The UPS Store discovered malware... at 51 locations in 24 states (about 1%) of 4,470 franchised center locations throughout the United States.
Customers' information, who used a credit or debit card at the 51 impacted franchised center locations between January 20, 2014 and August 11, 2014, may have been exposed.
The customer information that may have been exposed includes names, postal addresses, email addresses and payment card information.
|
The time intervals between card data breaches are rapidly decreasing. The day is not far off when we start getting a news like this every day, or even several times a day, because there is nothing that realistically can stop hackers from breaking into the stores and point-of-sale machines. The payment card technology is insecure by design, and there is no easy and cheap solution for this problem.
0 Comments
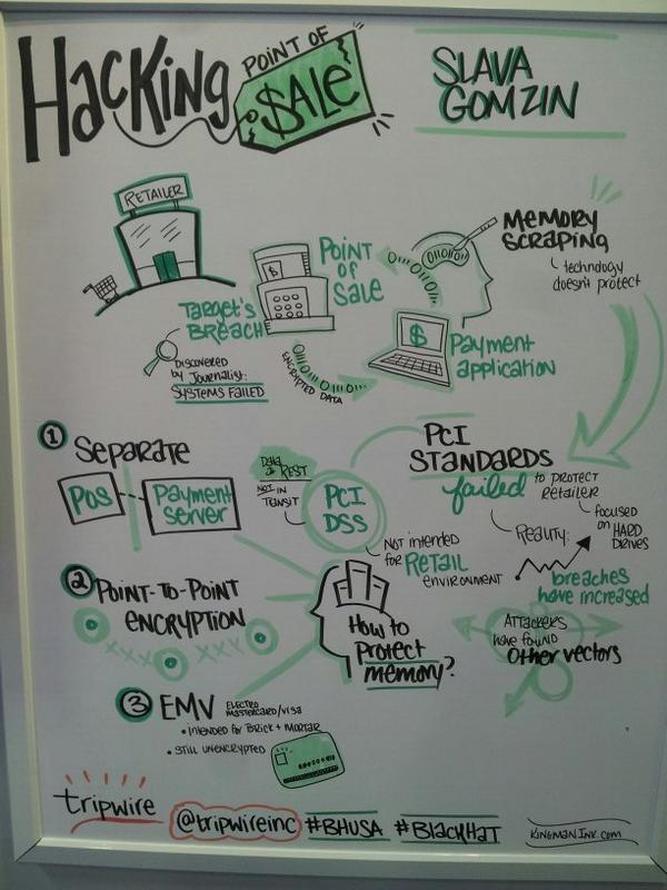
 Venture Beat just published my review of the situation with payment card security, which basically answers the question: are we going to see more card data breaches? Supervalu and Albertsons are the latest retail chains to get hit by credit card breaches, but they won’t be the last. Here's why. Just another grim story in the row of card data breaches... We will see more and more breaches like this until the industry realizes that the current payment card technologies - EMV is no exception - are insecure by design, it is nearly impossible to patch them, and they should be replaced by something else! This is visual representation of my Hacking Point of Sale talk at Tripwire booth at Black Hat USA 2014. Thanks Tripwire for this opportunity to present and sign the book! I'll be doing two one-hour book signings at Black Hat USA 2014 and DEF CON 22 conferences in Las Vegas: Black Hat USA 2014: August 6, 2014, 5:30 pm Mandalay Bay Conference Center, Tripwire booth 141 (I'll be doing a short presentation before the book signing) DEF CON 22: August 8, 2014, 11:00 am Rio Hotel & Casino, No Starch Press community table in Vendor Area Can someone shed light on this ghostly "payment card industry fraud investigative unit"? I stumbled upon this name in Brian Krebs blog's post about potential card data in Goodwill Industries. But googling this name did not return any distinct reference. Isn't such a unit, if it really exists, supposed to have some kind of communication portal for public relations, like IC3, for example? According to this study, more than 63% of businesses do not encrypt the account numbers of payment cards. Isn't it a true hacker heaven? During its 2014 study, PANscan scanned 145,144 gigs of data on 2,590 computers and found: PCI SSC to release version 2.0 of P2PE (Point-to-point Encryption) security standard during 2014. The goal is to increase market acceptance of P2PE technology while maintaining the high security level of its implementations. The new version of the standard is supposed to be more understandable, contain less requirements, and clarify the validation process for solution providers. P2PE v.2.0 will also combine both Hardware/Hardware and Hardware/Hybrid standards (the difference is that HW/HW requires both encryption and decryption to be performed in cryptographic hardware, while HW/Hybrid allows some parts of decryption process to be done in software). Hybrid encryption (do not confuse with hybrid decryption), Software Encryption, and Software Decryption options will be discontinued due to security concerns. P2PE is the PCI Security Standard Council’s most recent standard (others include PCI DSS, PA-DSS, and PTS) for merchants, HW/SW vendors, and service providers. Although the first version of the standard was released almost 3 years ago (in September 2011), due to complexity and uncertainty of multiple PCI P2PE requirements only 3 companies are currently listed on the PCI website as certified P2PE solution providers. The idea of Coin is simple but elegant: replacing several payment cards with single card-like sophisticated device. The technology behind Coin is pretty impressive, but there is security concern. Normally, when carders want to use the stolen card data in order to make a purchase in brick-and-mortar store, they need to produce the fake plastic card, which looks like a real credit card, and encode it with the stolen magnetic tracks. However, technological revolution comes to the carders world. With Coin, there is no need to produce a good looking physical plastic anymore. The stolen data can be encoded directly into the Coin device. There is one obstacle that must be overcome - taking the picture of the real card when entering the new card information into Coin through the iPhone or Android app. But I think that generating a realistic image of the credit card (so it could be photographed instead of the real card) is cheaper than creating a physical counterfeited card which requires special equipment such as PVC-printer, embosser, tipper, etc. (more details about this process can be found in my new book - Hacking Point of Sale - which is being published by Wiley). |
Books
 Crypto Basics Crypto Basics
 Bitcoin for Nonmathematicians: Exploring the Foundations of Crypto Payments Bitcoin for Nonmathematicians: Exploring the Foundations of Crypto Payments
 Hacking Point of Sale: Payment Application Secrets, Threats, and Solutions Hacking Point of Sale: Payment Application Secrets, Threats, and Solutions
Recent Posts
Categories
All
Archives
March 2023
|





 RSS Feed
RSS Feed
