
 The article is called These new mobile wallet apps will make it easier, not harder, for hackers to hijack your payment card and it's focused on two mobile payment solutions: Coin and Loop. When I started reviewing those technologies and their security features, I noticed that there are potential security vulnerabilities "hidden" in those solutions. The trick is that those vulnerabilities are not threatening directly the consumers or merchants, but they may affect the already weak security of the card payment system itself.
0 Comments
Interesting list of 10 examples of BLE Beacons implementations, including payments (PayPal "hands-free"). My interview by Cathleen McCarthy at CreditCards.com about recent breaches, payments with credit/debit cards, EMV migration, etc. Secure payments with HP Mobile POS: Implementing point-to-point encryption using HP retail solutions3/7/2014 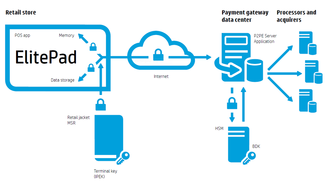 Secure payments with HP Mobile POS: Implementing point-to-point encryption using HP retail solutions is the technical whitepaper which I have created for HP. More information about HP mobile POS solutions can be found here. Download PDF Executive Summary This is second shutdown event of Bitcoin service provider after recent online exchange Mt. Gox bankruptcy caused by the flaw in Bitcoin transaction processing design. According to the message on Flexcoin website, they are closing their business but still going to publish the details of the attack as soon as they are available.  I was interviewed about recent card data breaches and my book - Hacking Point of Sale. You can listen to the interview here. Thanks to ITS Partners, and personally - to Jacob Crawford (@jake_crawford91) for this interview and for the great quality of the podcast! |
Books
 Crypto Basics Crypto Basics
 Bitcoin for Nonmathematicians: Exploring the Foundations of Crypto Payments Bitcoin for Nonmathematicians: Exploring the Foundations of Crypto Payments
 Hacking Point of Sale: Payment Application Secrets, Threats, and Solutions Hacking Point of Sale: Payment Application Secrets, Threats, and Solutions
Recent Posts
Categories
All
Archives
March 2023
|




 RSS Feed
RSS Feed
