|
I have created a separate menu entry -- "PCI ISA" -- which contains a link to the one of the most popular blog entries - PCI ISA Training Experience. So everyone can just click on the direct menu link and share her/his experience about ISA certification process - training, exam, and more.
0 Comments
I just published the Mobile Checkout - secure mobile payments solution proposal which I created (along with the working proof of concept) back in 2009.
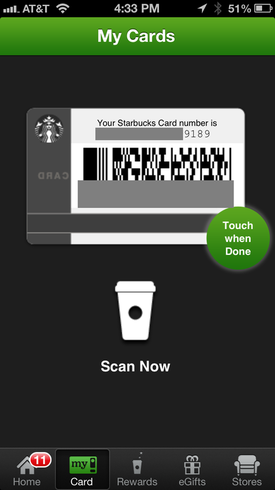
Compare it with Starbucks Mobile App - can you see any similarity? (No, I have never sent this proposal to Starbucks... Unfortunately... ) However, there is a big difference as well: in my solution, the card number was not displayed on the mobile phone screen as it is done in Starbucks app (xxxxxxxxxxxx9189 in the screenshot below). My app was displaying just 4 digits - simple randomly generated token (4067 in the screenshot below) which becomes useless as soon as the barcode is scanned (or the 4 digits are keyed) by cashier and the mobile device is linked with the point of sale transaction. The actual payment card number was never exposed to the mobile device and point of sale because the transaction was processed in a cloud between mobile app and point of sale servers. I just found a list of "PCI myths" on some website about PCI compliance. One of the myths sounds familiar and reasonable, although the explanation (they call it "fact") sounds polite but unconvincing and incomplete: Myth: PCI will make us secure. Fact: Successful completion of a system scan or assessment for PCI is but a snapshot in time. Security exploits are non-stop and get stronger every day, which is why PCI compliance efforts must be a continuous process of assessment and remediation to ensure safety of cardholder data. The popular Costa Rica based online payment system Liberty Reserve went down following the arrest of his founder Arthur Budovsky (Артур Будовский). Budovsky, 39, a former U.S. citizen and naturalized Costa Rican of Ukrainian origin, was arrested in Spain as part of a money laundering investigation.
I found interesting U.S. Department of Justice report about money laundering in digital currencies. In addition to information about the money laundering payment systems, it explains in an accessible form the methods of anonymous Internet access: Various technologies can increase the utility of digital currencies for money laundering by providing additional anonymity and networking abilities. Because digital currency transactions are conducted over the Internet, they can be traced back to individuals’ computers. The origins of Internet activity can often be identified using IP (Internet Protocol) addresses. Each computer on a network, including the Internet, must be uniquely identified by an IP address in order to receive information, such as web pages, requested from remote servers. These servers, including digital currency servers, track and record users’ IP addresses. However, anonymizing proxy servers and anonymity networks protect individuals’ identities by obscuring the unique IP (Internet Protocol) address as well as the individuals’ true locations. Anonymizing proxy servers and anonymity networks are designed to prevent identification of Internet users’ IP addresses. Such proxy servers and networks redirect users’ activities so that they appear to originate from a proxy server’s or anonymity network’s IP address rather than the IP address of an individual Internet user. Furthermore, mobile payments conducted from anonymous prepaid cellular devices, such as web-enabled phones, may be impossible to trace to an individual. Such portable devices that provide Internet access enable transfers of digital currency; afterward, they can be destroyed, easily and inexpensively, to prevent forensic analysis. |
Books
 Crypto Basics Crypto Basics
 Bitcoin for Nonmathematicians: Exploring the Foundations of Crypto Payments Bitcoin for Nonmathematicians: Exploring the Foundations of Crypto Payments
 Hacking Point of Sale: Payment Application Secrets, Threats, and Solutions Hacking Point of Sale: Payment Application Secrets, Threats, and Solutions
Recent Posts
Categories
All
Archives
March 2023
|
Slava Gomzin





 RSS Feed
RSS Feed
