| All this code is doing is attempting to connect to the domain we registered: if the connection is not successful it ransoms the system; if it is successful the malware exits. The reason that was suggested is that the domain is a “kill switch” in case something goes wrong, but I now believe it to be a badly thought out anti-analysis. In certain sandbox environments traffic is intercepted by replying to all URL lookups with an IP address belonging to the sandbox rather than the real IP address the URL points to. A side effect of this is if an unregistered domain is queried it will respond as it it were registered (which should never happen). I believe the malware creators were trying to query an intentionally unregistered domain which would appear registered in certain sandbox environments, then once they see the domain responding, they know they’re in a sandbox and the malware exits to prevent further analysis. This technique isn’t unprecedented: the Necurs trojan queries five totally random domains, and if they all return the same IP it exits. However, because WannaCrypt used a single hardcoded domain, my registration of it caused all infections globally to believe they were inside a sandbox and exit... thus we unintentionally prevented the spread and further ransoming of computers infected with this malware. Of course now that we are aware of this, we will continue to host the domain to prevent any further infections from this sample. One thing that is very important to note is our sinkholing only stops this version of the ransomware, and there is nothing stopping them removing the domain check and trying again, so it’s incredibly important that any unpatched systems are patched as quickly as possible. |
|
1 Comment
The beauty of Bitcoin is not just its ability to anonymously and safely handle darknet market payments like ones demanded by now popular ransomware WannaCry. Another interesting feature of Bitcoin is its ability to provide everyone else with detailed information about the number and amount of those payments as Bitcoin Blockchain is available publicly. WannaCry's Bitcoin addresses are hardcoded, which is kind of stupid but entertaining.
Bitcoin anonymity ends when you need to convert this virtual currency to old good bucks. However, there are still some options available to resolve this issue. First, you can keep the virtual currency and use it on darknet markets. Second, there are special tools called anonimizers which can mix multiple addresses and transactions in order to launder Bitcoins. Currently, there are about 32 bitcoints on those accounts which equals to ~ $55,000. Here are the WannaCry Bitcoin accounts: https://blockchain.info/address/13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94 https://blockchain.info/address/12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw https://blockchain.info/address/115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn
The list of top ten web application vulnerabilities has been updated for the first time since 20134/28/2017 The release candidate of OWASP Top 10 vulnerabilities of web applications for 2017 has been published on the OWASP website. Injections (like SQL injection or code injection) are still #1 threat for web apps, no changes here since 2013.
There is interesting phishing method that is described here. It is also called homograph attack. Many English (Latin) domain names can be represented by Russian (Cyrillic) letters which look almost the same but their character codes (Unicode) are different. So you think you are seeing the legitimate domain name like apple.com, but in reality it is fake name which looks exactly the same as the original name. The only thing I did not fully understand is how they represent latin letter "l" (lower case "L") as there is no similar letter in Cyrillic. I guess they just use "1" (number "one") instead of "l" but it still can be recognized?
a - Cyrillic letter "a" р - Cyrillic letter "r" р - Cyrillic letter "r" 1 е - Cyrillic letter "e" . с - Cyrillic letter "s" о - Cyrillic letter "o" м - Cyrillic letter "m"
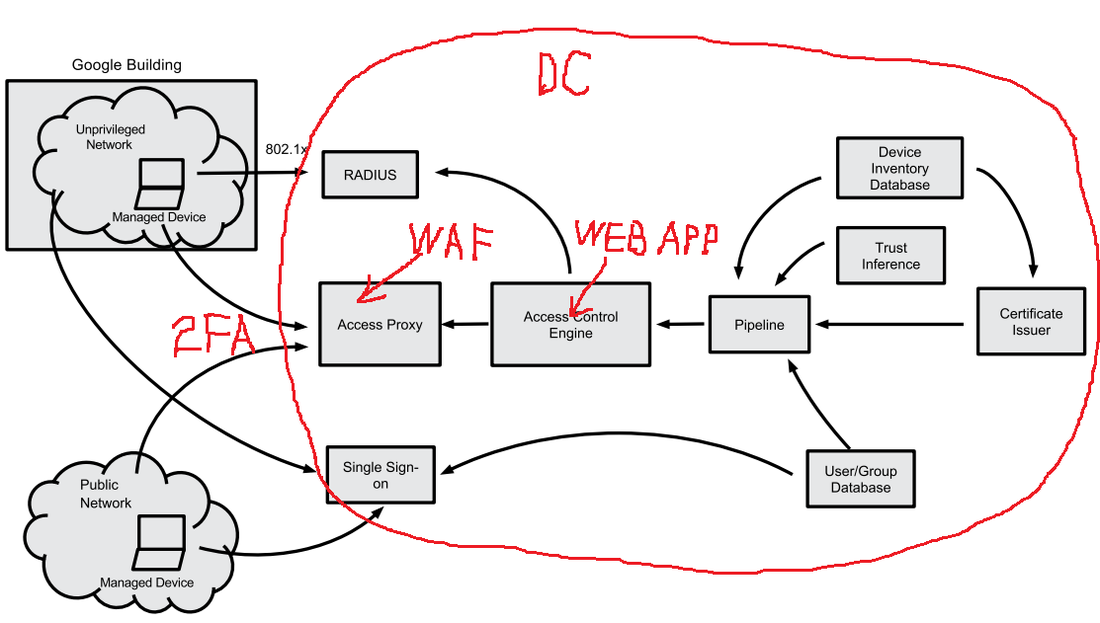
Interesting article about new Google approach to access control for enterprise applications. I agree with their approach because it seems that BeyondCorp is neither more nor less than just another implementation of web app with two factor authentication (2FA) by client certificates plus Web Application Firewall (WAF) functionality and some elements of risk based authentication, so there is nothing really revolutionary. I guess it fits mostly large enterprises as it requires significant additional hardware, software, and human resources (I like the author’s job title – “site reliability engineering manager”), unless there will be specialized hardware/software/services which are designed, implemented, and supported by third party vendors (Google?).
Note that the “privileged networks” still exist “behind the scenes” – in order to support all internal application deployments (such as database servers, etc.) and access control infrastructure. In fact, all the BeyondCorp elements in Figure 1 (see below) are located in privileged network, which is still accessed using “old fashion” ways such as remote VPN etc. Only the front end (they call it “access proxy”) is accessible from “unprivileged network”, so there is nothing unique in this model – in fact, it is used by most web applications hosting providers who can say that they are implementing some limited version of BeyondCorp too. In a typical simplified case, the provider's data center (DC) environment is such a "privileged network", which serves the web applications’ back end and access control infrastructure (see red marks in the picture below). WAF can be used as an “access proxy”. The second authentication factor -- such as SMS, email, or Google Authenticator -- is a replacement for the device certificates utilized by BeyondCorp (which are just another classic example of the second “something you have” authentication factor implementation). The only element that is probably missing is the risk-based authentication, but there is always room for improvement. If you are not familiar with Tor yet you should learn about it. In a nutshell, Tor is a system for anonymous Internet browsing. You can install Tor software and browse the Internet anonymously. If you are using Tor along with Bitcoin, you can enjoy the Internet freedom and privacy. This is Kickstarter project which is supposed to create the Tor hardware box. Anonabox should be more safe and convenient than Tor software as it routes all the traffic from your Ethernet connection through Tor network. I like this excerpt from Dan Geer's keynote at Black Hat USA 2014: Our choices are Freedom, Security, Convenience -- Choose Two The full transcript of the keynote is available here. I'll be doing two one-hour book signings at Black Hat USA 2014 and DEF CON 22 conferences in Las Vegas: Black Hat USA 2014: August 6, 2014, 5:30 pm Mandalay Bay Conference Center, Tripwire booth 141 (I'll be doing a short presentation before the book signing) DEF CON 22: August 8, 2014, 11:00 am Rio Hotel & Casino, No Starch Press community table in Vendor Area Can someone shed light on this ghostly "payment card industry fraud investigative unit"? I stumbled upon this name in Brian Krebs blog's post about potential card data in Goodwill Industries. But googling this name did not return any distinct reference. Isn't such a unit, if it really exists, supposed to have some kind of communication portal for public relations, like IC3, for example? |
Books
 Crypto Basics Crypto Basics
 Bitcoin for Nonmathematicians: Exploring the Foundations of Crypto Payments Bitcoin for Nonmathematicians: Exploring the Foundations of Crypto Payments
 Hacking Point of Sale: Payment Application Secrets, Threats, and Solutions Hacking Point of Sale: Payment Application Secrets, Threats, and Solutions
Recent Posts
Categories
All
Archives
March 2023
|





 RSS Feed
RSS Feed
