This is Kickstarter project which is supposed to create the Tor hardware box. Anonabox should be more safe and convenient than Tor software as it routes all the traffic from your Ethernet connection through Tor network.
|
If you are not familiar with Tor yet you should learn about it. In a nutshell, Tor is a system for anonymous Internet browsing. You can install Tor software and browse the Internet anonymously. If you are using Tor along with Bitcoin, you can enjoy the Internet freedom and privacy. This is Kickstarter project which is supposed to create the Tor hardware box. Anonabox should be more safe and convenient than Tor software as it routes all the traffic from your Ethernet connection through Tor network.
0 Comments
I like this excerpt from Dan Geer's keynote at Black Hat USA 2014: Our choices are Freedom, Security, Convenience -- Choose Two The full transcript of the keynote is available here. I'll be doing two one-hour book signings at Black Hat USA 2014 and DEF CON 22 conferences in Las Vegas: Black Hat USA 2014: August 6, 2014, 5:30 pm Mandalay Bay Conference Center, Tripwire booth 141 (I'll be doing a short presentation before the book signing) DEF CON 22: August 8, 2014, 11:00 am Rio Hotel & Casino, No Starch Press community table in Vendor Area Interesting opinion on application of Beacons technology in retail. I would agree. if it’s not executed properly, it could be interpreted as a violation of privacy it’s highly untested, and improper execution could do more harm than good. beacons border “on the edge of cool and creepy” Is Bitcoin going to be the future technology of online payments? And maybe not just online? Bitcoin hit a high of $1,073 on Tokyo- based exchange Mt. Gox, the best-known operator of a bitcoin digital marketplace, compared with just below $900 the previous day. Bitcoin is not backed by physical assets and is not run by any person or group. Its value depends on people's confidence in the currency. It has been gaining acceptance by the general public and investment community but has yet to become an accepted form of payment on the websites of major retailers such as Amazon.com. According to a a patent application filed by Apple, the entire display can be used to read your fingerprints. I can imagine a lot of use cases, including payments security, beyond just the iPhone screen. For example, super strong 3-factor authentication when processing payment transaction: 1. card ("something you have") 2. PIN ("something you know") 2. Fingerprints while entering PIN ("something you are"). Or another case - PIN-less payment transaction that keeps security level (2-factor authentication) of PIN transaction: card or phone (the 1st factor - "something you have") plus pressing the "Pay" or "OK" button on payment terminal or mobile phone with simultaneous fingerprint scanning (2nd factor - "something you are"). The idea of Coin is simple but elegant: replacing several payment cards with single card-like sophisticated device. The technology behind Coin is pretty impressive, but there is security concern. Normally, when carders want to use the stolen card data in order to make a purchase in brick-and-mortar store, they need to produce the fake plastic card, which looks like a real credit card, and encode it with the stolen magnetic tracks. However, technological revolution comes to the carders world. With Coin, there is no need to produce a good looking physical plastic anymore. The stolen data can be encoded directly into the Coin device. There is one obstacle that must be overcome - taking the picture of the real card when entering the new card information into Coin through the iPhone or Android app. But I think that generating a realistic image of the credit card (so it could be photographed instead of the real card) is cheaper than creating a physical counterfeited card which requires special equipment such as PVC-printer, embosser, tipper, etc. (more details about this process can be found in my new book - Hacking Point of Sale - which is being published by Wiley). Biometric scanner on mobile phone is interesting feature that might be helpful to enhance security of mobile payments, as well as simplify the payment process and reduce the transaction processing time.
I just published the Mobile Checkout - secure mobile payments solution proposal which I created (along with the working proof of concept) back in 2009.
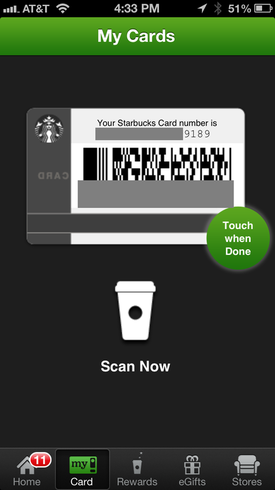
Compare it with Starbucks Mobile App - can you see any similarity? (No, I have never sent this proposal to Starbucks... Unfortunately... ) However, there is a big difference as well: in my solution, the card number was not displayed on the mobile phone screen as it is done in Starbucks app (xxxxxxxxxxxx9189 in the screenshot below). My app was displaying just 4 digits - simple randomly generated token (4067 in the screenshot below) which becomes useless as soon as the barcode is scanned (or the 4 digits are keyed) by cashier and the mobile device is linked with the point of sale transaction. The actual payment card number was never exposed to the mobile device and point of sale because the transaction was processed in a cloud between mobile app and point of sale servers. The popular Costa Rica based online payment system Liberty Reserve went down following the arrest of his founder Arthur Budovsky (Артур Будовский). Budovsky, 39, a former U.S. citizen and naturalized Costa Rican of Ukrainian origin, was arrested in Spain as part of a money laundering investigation.
I found interesting U.S. Department of Justice report about money laundering in digital currencies. In addition to information about the money laundering payment systems, it explains in an accessible form the methods of anonymous Internet access: Various technologies can increase the utility of digital currencies for money laundering by providing additional anonymity and networking abilities. Because digital currency transactions are conducted over the Internet, they can be traced back to individuals’ computers. The origins of Internet activity can often be identified using IP (Internet Protocol) addresses. Each computer on a network, including the Internet, must be uniquely identified by an IP address in order to receive information, such as web pages, requested from remote servers. These servers, including digital currency servers, track and record users’ IP addresses. However, anonymizing proxy servers and anonymity networks protect individuals’ identities by obscuring the unique IP (Internet Protocol) address as well as the individuals’ true locations. Anonymizing proxy servers and anonymity networks are designed to prevent identification of Internet users’ IP addresses. Such proxy servers and networks redirect users’ activities so that they appear to originate from a proxy server’s or anonymity network’s IP address rather than the IP address of an individual Internet user. Furthermore, mobile payments conducted from anonymous prepaid cellular devices, such as web-enabled phones, may be impossible to trace to an individual. Such portable devices that provide Internet access enable transfers of digital currency; afterward, they can be destroyed, easily and inexpensively, to prevent forensic analysis. |
Books
 Crypto Basics Crypto Basics
 Bitcoin for Nonmathematicians: Exploring the Foundations of Crypto Payments Bitcoin for Nonmathematicians: Exploring the Foundations of Crypto Payments
 Hacking Point of Sale: Payment Application Secrets, Threats, and Solutions Hacking Point of Sale: Payment Application Secrets, Threats, and Solutions
Recent Posts
Categories
All
Archives
March 2023
|






 RSS Feed
RSS Feed
